IV Quantum Communication
Quantum communication concerns the transfer of information, and uses entanglement as a resource in order to achieve classically impossible tasks. In the sections below we discuss three examples: the transmission of two bits of information by sending a single qubit (superdense coding); the transfer of the quantum state of one qubit to another qubit at a distant location (teleportation), and the generation of unbreakable encryption codes for secure communication. All these tasks can be achieved with current technology.
IV.1 Superdense coding
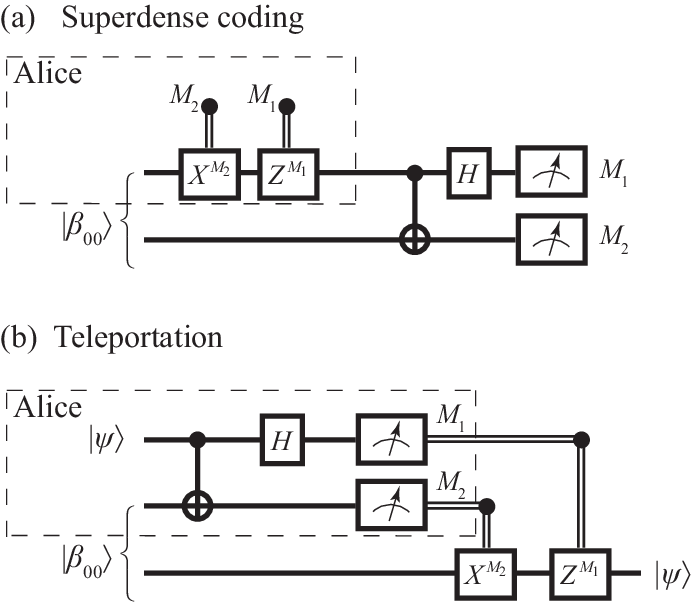
Superdense coding is a simple scheme which illustrates how entanglement can facilitate the transmission of information. The scheme is illustrated in Fig. 9(a). Here and in the following, double-lines indicate classical transmission or control channels. By convention, sender and receiver are designated the names Alice and Bob (or A and B), respectively. Initially, Alice and Bob each are in possession of a single qubit. In the distant past (say), they met and prepared these qubits in the entangled Bell state . Now, Alice and Bob are located at distant locations (this handed down tale is intended to convey how the scheme will exceed classical expectations, but most of these embellishments are not necessary—e.g., A&B could have received their entangled qubits from an appropriate, distantly located two-photon source). Alice can now decide whether she wishes to carry out two operations on her qubit—first a NOT operation (), then a phase flip (). This results in the state , where if the operation was carried out, and if it was not carried out. Considering each case separately, we see that this transforms the state into , i.e., into one of the four Bell states. Alice then sends her qubit—just the single one—to Bob, who can use a CNOT and a Hadamard gate to transform the qubit pair back to the computational basis states, [this is just the inverse of the entanglement procedure in Fig. 6(a)]. A measurement of both qubits in the computational basis therefore allows him to infer both and . In effect, using entanglement as a resource, Alice has sent Bob two bits of information.
IV.2 Quantum teleportation
Quantum teleportation addresses the task of transferring the unknown and arbitrary state of one qubit to another, possibly distant qubit. Because of the no-cloning theorem, this requires to erase all information from the first qubit. How this can be achieved is shown in Fig. 9(b). Before considering the details, note the striking similarities to the circuit for superdense coding—most notably, Alice and Bob again share a Bell pair, and the set of operations they carry out is just interchanged. However, Alice is now also in possession of an extra qubit, whose state she wishes to transmit to Bob. She does not know the complex amplitudes and , and she cannot send the qubit itself, but she can send classical information along a transmission line (e.g., by phone). To succeed, she first entangles the two qubits in her possession by applying a CNOT and a Hadamard gate. This results in the three-qubit state
where the second line follows by reordering the terms. Next she measures the two qubits in her possession, and sends her measurement results and to Bob. This allows him to infer how the post-measurement state of his qubit is related to the former state :
Therefore, in order to obtain , he simply applies to his qubit.
IV.3 Secure communication
Secure quantum communication schemes rely on the no-cloning theorem, which prevents an eavesdropper (’Eve’) to listen to a communication line (either, Eve will not acquire any information, or her actions can be detected).
Secure communication based on superdense coding.—If Eve would intercept the qubit sent between Alice and Bob, she only possesses a qubit with reduced density matrix , which is independent on the two bits and that Alice is sending. However, Eve could still send an arbitrary qubit to Bob, which would result in him obtaining random values for and , as well. This can be detected when Alice and Bob compare parts of their messages.
Quantum key distribution.—To make communication both secure and reliable, one can generate an encryption key shared by Alice and Bob. The message can then be sent classically using a simple encryption technique (e.g., by using XOR operations, which flips bits according to a shared sequence of 0’s and 1’s.).
(a) The BB84 protocol (due to Bennett and Brassard) is a protocol that does not require entanglement. Alice prepares qubits randomly in one of the following four states:
These are the eigenstates of the and operator. Alice makes sure that she uses a preparation method that tells her which state she has prepared (e.g., this can be done by making random and measurements on qubits with density matrix ). She then sends these qubits to Bob, who, for each qubit, randomly measures either or . When he measures and the qubit was in state , he will obtain 1 with certainty, while if the state was , he will obtain with certainty. If the state was or , he will obtain 1 or with 50% probability. In contrast, if Bob measures , he will obtain certain measurement outcomes 1 and for the states and , respectively, while the states result in random measurement outcomes. Bob now tells Alice which measurements he did for each qubit, and Alice tells Bob which measurements she did to prepare the qubits (they only communicate the type of measurement, or , but not their outcomes). For these instances, their measurements will have resulted in the same outcome, which results in a shared sequence of 0’s and 1’s that they can use for encryption.
An eavesdropper listening to the key distribution would be able to make measurements on an intercepted qubit, but without knowledge of its preparation would not be able to then forward the same qubit to Bob. This would introduce errors into the key (at a rate of 25%), which can be detected when Alice and Bob compare small samples of their key (this part of the key would then be discarded).
The BB84 scheme is simple and robust, and has been implemented experimentally using photons, for which the four states correspond to polarizations in , , , and direction. (E.g., in 1997, the scheme was demonstrated using a 23 km long transmission line beneath Lake Geneva.)
(b) The EPR protocol (due to Eckert) uses pairwise entangled qubits prepared in the Bell state , which can also be written as . Alice and Bob make random measurements of and on each of their qubits, and then communicate to each other to find out for which qubits they did the same measurement. For each of these instances, they are then guaranteed to have found the same outcome. Again, an eavesdropper would introduce errors, and can be detected by sacrificing a small random sample of the key.
In combination with classical encoding schemes that encode messages into longer bit sequences (see error correction, in section VI.1) these protocols can be made reliable against a finite error rate, and secure even against sophisticated eavesdroppers attacks that involve the collective manipulation of the whole qubit stream.