III Quantum information representation and manipulation
This section introduces quantum bits (qubits) and quantum gates, and discusses some underlying concepts such as quantum parallelism (arising from the superposition principle), entanglement as a resource for computation, and the no-cloning theorem. These concepts clearly distinguish quantum computers from classical computers, and are the reason why (in principle) the former are far more powerful than the latter.
III.1 Quantum bits
Quantum computers encode information into the quantum state of a composite system, consisting of a number of two-state systems known as qubits (quantum bits). Taken individually, each qubit can be described by a quantum state . The basis states and form the computational basis, and represent classical bits with values 0 and 1. What is special about qubits is that their general state can also be a superposition of 0 and 1, which cannot be realized by a classical bit. In this case, and give the probabilities to find 0 or 1 in a measurement of the qubit in the computational basis [associated with the operator ], which on the Bloch sphere depend on the polar angle . Measurements of other observables (like or ) give access to other combinations of and , which also depend on the phase of the qubit. However, since measurements change the state of the qubit, it is not possible to directly encode information into the complex numbers and ; this distinguishes quantum computers from analog computers.
An -bit quantum register contains qubits. The state of the register is then formed using the computational basis states , where is the binary code of numbers ranging from to . Here, we will not drop leading zeros (thus, for we write 0010 for the decimal number 2) because they describe the state of some of the qubits. Sometimes, we denote these states by the corresponding numbers ; e.g., for a 4-bit register, and .
Just as the individual qubits, the register may be brought into a superposition of the computational basis states. For instance, one can form the state
which contains all binary numbers between 0 and at the same time. All these numbers therefore can be manipulated at once by a single physical operation on the register. This feature is sometimes described as quantum parallelism, and will be frequently exploited in Section V.
The state given above is still separable, and therefore can be obtained by operating on the individual qubits. The real power of the register is unleashed when one considers that the qubits in the register can also be entangled, which can be achieved by manipulating pairs of qubits. We next explore how entanglement is linked to information and then have a look at a number of basic quantum operations on the register which enable to exploit these special features of qubits.
III.2 Quantum information
Quantum mechanically, the entropy of a system with density matrix is given by the von Neumann entropy
This is identical to the Shannon entropy, with the probabilities replaced by the eigenvalues of . It follows that a system in a pure state has von-Neumann entropy .
Classically, the entropy of a subsystem is always less than the entropy of a composite system with parts and : . Quantum mechanically, the entropy of a subsystem follows by inserting the reduced density matrix, and can be larger than the entropy of a composed system. This is in particular the case when an entangled systems is in a pure state. The entropy of the composite system vanishes, but it is finite for each of its parts because the reduced density matrices are mixed (see section I.7). For composite systems that are already in a mixed state, this leads to the more sophisticated measures of entanglement also mentioned in that section.
In terms of data compression, the von Neumann entropy plays a similar role as the Shannon entropy: it describes how many qubits are necessary to transmit a certain amount of (quantum) information (this can be quantified via Schumacher’s noiseless channel coding theorem).
How much information can be transmitted via a single qubit? Assume that the incoming data stream is composed of states described by a density matrix , which can be assumed to be mixed because of limitations in the preparation or transmission of the qubit states. It then can be shown that the maximally accessible amount of information per qubit cannot exceed a certain limit, , where , and is the fraction of qubits with density matrix . This inequality is known as the Holevo bound, and the quantity is the Holevo information. Note that when all are pure, , and therefore .
The Holevo bound implies that a single qubit cannot transmit more than one bit of classical information. However, as embodied by the superdense coding scheme discussed next, if sender and receiver possess as an additional resource a number of shared entangled qubits, it is possible to transmit two bits of classical information via a single (entangled) qubit. Indeed, the applications below show that entanglement is a useful, non-classical resource for communication. Entanglement can also be used for error correction schemes, as will be discussed in section VI.1.
In order to quantify entanglement of a (many-body) state , it is useful to determine how many maximally entangled Bell pairs one could generate (by local operations within each subsystem, and classical communication) if one had many copies of the state . This results in the entanglement of formation, which is an additive measure of entanglement, and therefore constitutes the appropriate counterpart to the information measure provided by the Shannon entropy. As discussed in Sec. I.7, for pure states the entanglement of formation simply reduces to the von Neumann entropy of the subsystems. This applies even for the case that each subsystem has more than two possible quantum states. For mixed states, however, explicit expressions are only known for some special cases, such as for two qubit-systems (see again Sec. I.7).
III.3 Quantum gates as unitary operations
Since solutions of the Schrödinger equation can be written as a time-dependent unitary transformation of the initial state, all quantum gates are represented by unitary operators, , where is the initial state of the register, and is the final state of the register. Computational algorithms furthermore complement these gates by mechanisms to prepare the register in an initial state, as well as mechanisms to read out the final state (which can be achieved by measurements). In the remainder of this section we concentrate on the unitary quantum gates.
First, a general observation: Because unitary operators can be inverted, all quantum gates are reversible: the input state can be inferred from . This also entails an important constraint onto quantum operations: The no-cloning theorem, according to which it is impossible to transfer the state of a control qubit to a target qubit without erasing the state of the control qubit.
Even though the quantum gates are reversible, a universal set of gates can be formed using only unary and binary gates; no three-bit gates are required. On the other hand, we need to consider a larger variety of such gates — besides achieving the classical logical tasks, we need gates that put qubits into non-classical superpositions of 0 and 1, and gates that establish entanglement between the qubits. Fortunately, this can be achieved by using a finite number of unary gates, plus a single binary gate. Circuit representations of these gates are shown in Fig. 3.

III.4 Single-qubit gates
All unary (single-qubit) gates can be represented as -dimensional unitary matrices, which act on the two component vector representing the state . Just as hermitian matrices, these can be generated by combining the Pauli matrices , , and , as well as the identity matrix . The latter leaves the state of the qubit unchanged, and therefore constitutes the quantum analogue to the identity gate . Furthermore, considering that and , represents the analogue to the classical NOT gate. For a general state of the qubit, application of this gate yields . Because they are irreversible, the two remaining classical unary gates ALWAYS TRUE/FALSE do not have unary quantum analogues.
Clearly, and do not exhaust all possible transformations of a qubit. On the Bloch sphere, represents a rotation by 180 about the axis, while leaves the state untouched. However, we can also operate, e.g., with , which flips the phase of the qubit (this advances the azimuthal angle by ). The most general single-qubit transformations correspond to rotations of the Bloch sphere about an arbitrary axis , by an arbitrary angle . Such general rotations can be written as
Fortunately, not all rotations are independent: E.g., following from the identity , (a 180 rotation about the axis) can be obtained by combining and (rotations about the and axis, respectively).
An example of a set of elementary rotations which can be combined to generate all possible rotations is given by the following three gates: the -gate
the phase gate
and the Hadamard gate
Here, and generate and rotations about the axis, respectively, while generates a rotation about the direction. Starting, say, from the initial state , these operations can be used to bring the qubit into any general superposition state .
Below, we will also often use -rotation gates about the axis, which have the form
III.5 Two-qubit gates
General two-qubit gates are represented by -dimensional unitary matrices, which act on the four component vector
representing a state .
The most important gate is the quantum version of the controlled-not gate CNOT, which negates the target qubit if the control qubit is in , and leaves the target unchanged if the control qubit is in ; the control qubit always remains in its initial state. If qubit 1 is the control bit, this is represented by the matrix
for reversed roles we have
Starting, say, from the separable state , we find , i.e., one of the Bell states. The CNOT gate can therefore be used to entangle two qubits.
In block notation, the matrix can also be written as . Replacing by an arbitrary unary gate delivers controlled versions of each unary gate, denoted as controlled- gates. An example is the controlled phase flip, which is obtained for . Another notable two-qubit gate is the quantum version of the SWAP gate, which is represented by the matrix
III.6 Composition of gates
In order to manipulate the information in the register, we need to apply unary and binary gates to the individual qubits. Unary gates operating on the th qubit in the register will be denoted by . Analogously, binary gates acting on qubits and will be denoted by . Here, order of the indices matters — in general, . In particular, for controlled gates, we will use the first index to refer to the control qubit, while the second index refers to the target qubit.
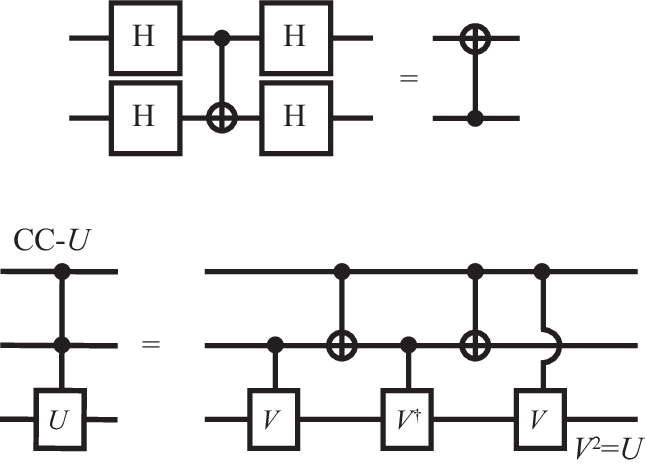
We can now combine unary and binary gates to achieve arbitrary operations on the register. For instance, the realization of the SWAP gate in terms of three CNOT gates, already known from the classical case, takes the form .
The combination of quantum gates allows to achieve tasks that would require more complicated gates if done classically. Some examples are listed in Fig. 4. Consider the operation , which first applies Hadamard gates to the two qubits, then acts with a CNOT gate, and finally again applies Hadamard gates. Using matrix multiplications, we find that for all initial states, this is equivalent to . Therefore, amazingly, decorating the gate with single-qubit operations allows to exchange the roles of the control and target qubits. Classically, this exchange would require additional binary gates. Similarly, we can obtain classical three-bit gates by combination of unary and binary gates. For instance, as shown in the figure, a general controlled-controlled- gate can be obtained by controlled- gates, where .

The Toffoli gate (controlled-controlled-not, CCNOT), which classically has to be introduced separately to achieve unversal reversible computations, follows for , such that . Just as in the classical case, the Fredkin gate is obtained by two additional CNOT operations, . Up to a phase factor, the Toffoli gate can also be achieved by using -rotations,
(see Fig. 5). Here, the phase factor changes the sign of the basis state , but leaves all other basis states unchanged.

Figure 6 shows combinations of gates which serve as frequent components of the quantum algorithms discussed in the following section. (a) The gate entangles qubits and that are initially prepared in computational basis states:
(b) Application of (i.e., acting with the Hadamard gate on each qubit) transforms an -qubit register with initial state into
the superposition of all states of the computational basis, which represents all binary numbers in the range of the register. (c) When the initial state is another computation basis state , the action of a Hadamard gate on an individual qubit can be written as
When we act with Hadamard gates on all the qubits in the register, we obtain the expression
where denotes the bitwise product of and .
III.7 Function gates


An important class of gates encountered in the following applications implement functions , where is an -bit input, and is an -bit output (see Fig. 7). In general, such functions are not invertible. The bottom panel of the figure shows a strategy to implement reversible versions of these functions: add auxiliary output channels which keep track of the input, and auxiliary input channels which when set to gives the desired outcome. (The auxiliary channels are called ancillas, and also feature prominently in error correction, section VI.1.) This can be achieved using the bit-wise XOR operation
Functions with single-bit output are called Boolean functions (because their output can be interpreted as 0=FALSE, 1=TRUE). If the input is also only a single bit, there are exactly four function gates, which can be implemented in terms of elementary gates as shown in Fig. 8. If the auxiliary input state is set to , they implement reversible versions of the four classical unary operators discussed in section II.5.